MFA Overview
Protecting Users in Groups from Being Compromised
Now that we have created users in groups, it is time for us to protect these users in groups from being compromised. For that, we have 2 defense mechanisms, which are:
- Password Policy
- Multi-Factor Authentication (MFA)
1. Password Policy
The stronger the password you use, the more security your accounts will have.
In AWS, you can set up a password policy with the following options:
- Set a minimum password length
-
Require specific character types, such as:
- Uppercase letter
- Lowercase letter
- Number
- Non-alphanumeric characters (e.g., a question mark)
Additional features of the password policy include:
- Allow or disallow IAM users from changing their own passwords
- Require users to change their password after a certain time period (e.g., every 90 days)
- Prevent password reuse, so users can’t change their password to one they’ve already used
A password policy is really helpful against brute force attacks on your account.
2. Multi-Factor Authentication (MFA)
MFA is the second defense mechanism and is highly recommended, especially for the root account and ideally for all IAM users.
Why use MFA?
Users may have access to your account and can do a lot of things:
- Change configurations
- Delete resources
So you want to add protection on top of the password by using an MFA device.
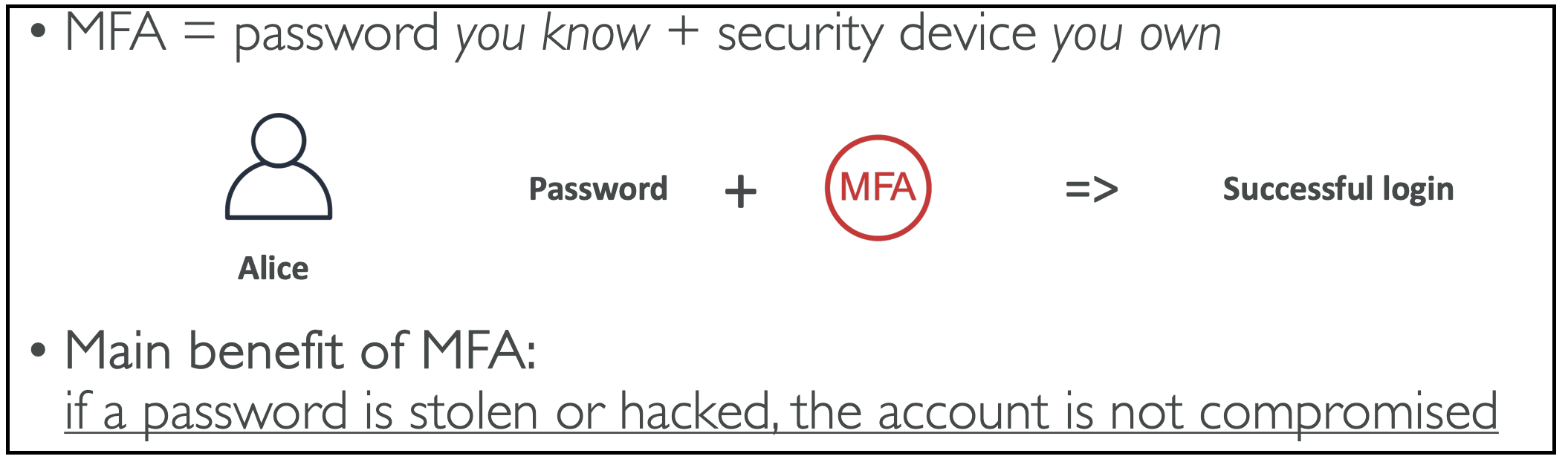
What is MFA?
MFA stands for Multi-Factor Authentication. It uses:
- Something you know: your password
- Something you own: a security device
Together, these provide greater security than just a password alone.
Example:
Let’s say Alice:
- Knows her password
- Has an MFA-generating token
By using both while logging in, she can successfully access her account. Even if Alice’s password is stolen, her account won’t be compromised unless the hacker also gets her physical device (like her phone).
MFA Device Options in AWS
You need to know the different MFA device types for the exam. They are:
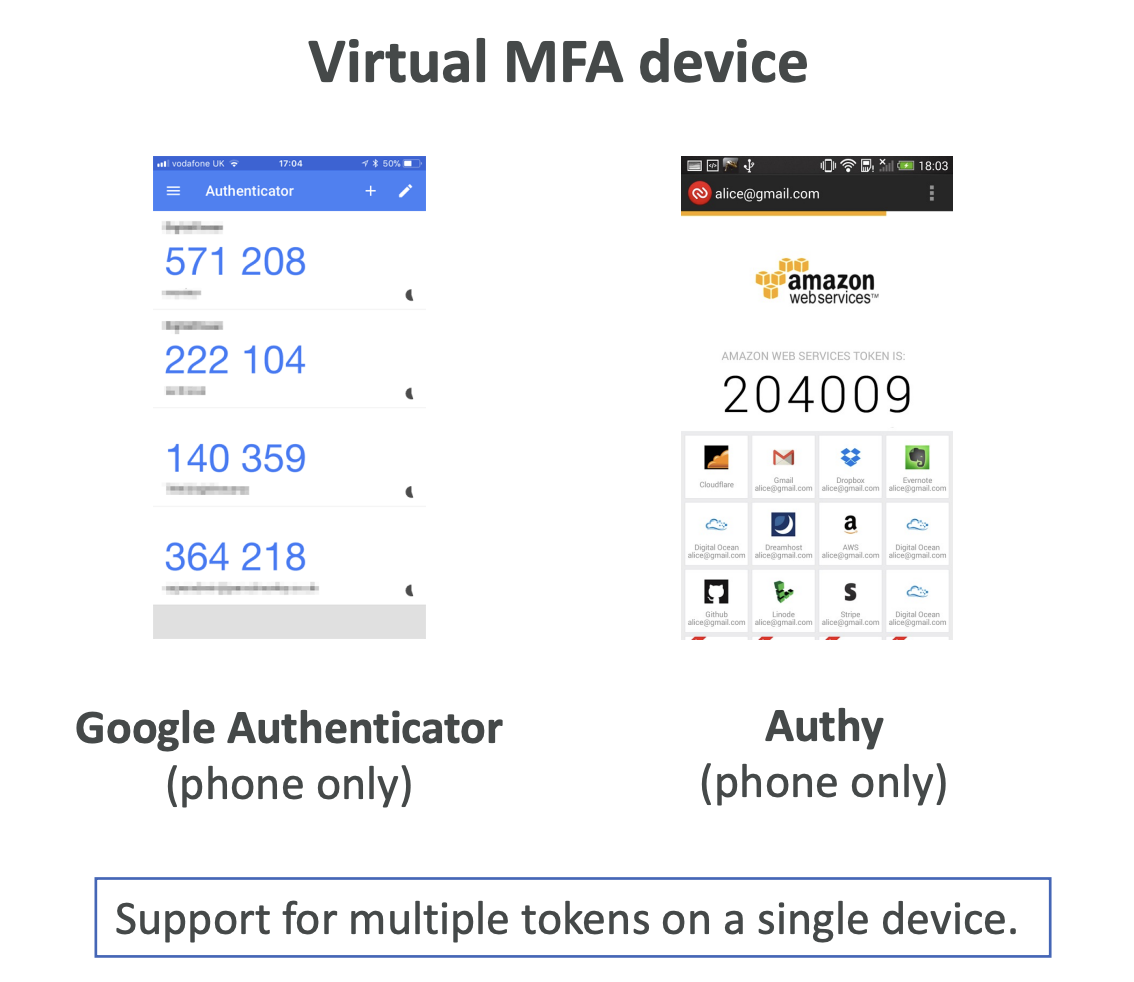
1. Virtual MFA Device
-
Works with apps like:
- Google Authenticator (works on one phone at a time)
- Authy (supports multiple tokens on a single device)
-
Can be used for:
- Root account
- IAM users
- Multiple accounts and users
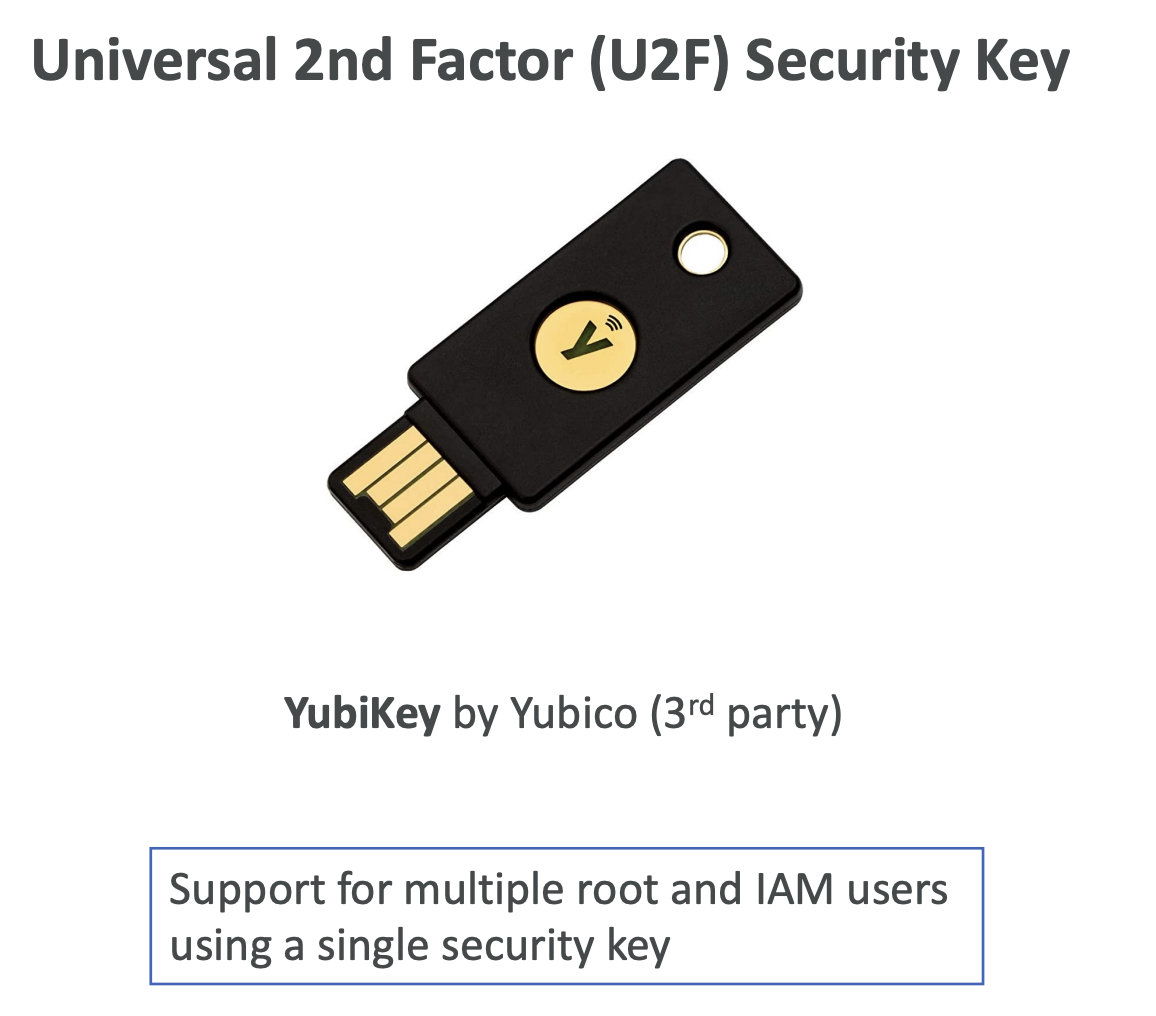
2. U2F Security Key
- Example: YubiKey by Yubico
- A physical device that plugs in (e.g., via USB)
- Third-party device, not provided by AWS
- Supports multiple root and IAM users on a single key
- Easy to carry, e.g., on key fobs
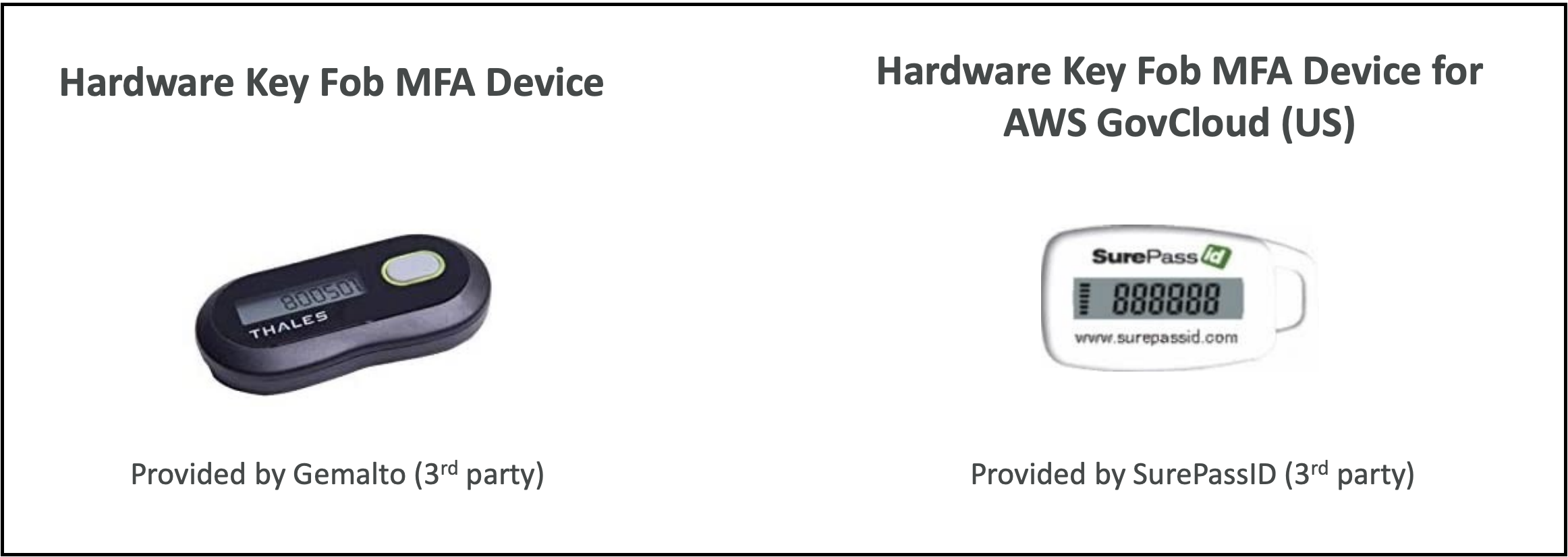
3. Hardware Key Fob MFA Device
- Example: device provided by Gemalto
- A third-party hardware MFA option
4. GovCloud MFA Device
- Used specifically for AWS GovCloud (US)
- Provided by SurePassID
- Special key fob for government cloud use
That’s it for the theory on how to protect your account.
➡️ In the next lecture, you will implement this in a hands-on lab.